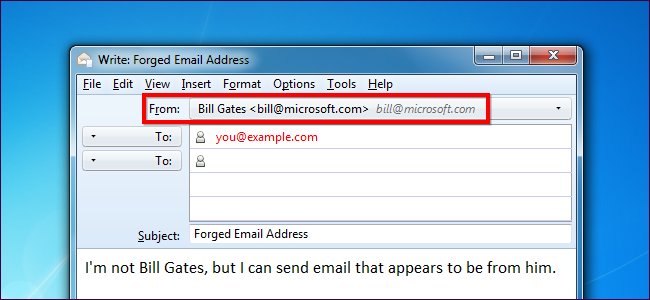
Consider this a public service announcement: Scammers can forge email addresses. Your email program may say a message is from a certain email address, but it may be from another address entirely.
Email protocols don’t verify addresses are legitimate — scammers, phishers, and other malicious individuals exploit this weakness in the system. You can examine a suspicious email’s headers to see if its address was forged.
How Email Works
Your email software displays who an email is from in the “From” field. However, no verification is actually performed – your email software has no way of knowing if an email is actually from who it says it’s from. Each email includes a “From” header, which can be forged – for example, any scammer could send you an email that appears to be from bill@microsoft.com. Your email client would tell you this is an email from Bill Gates, but it has no way of actually checking.
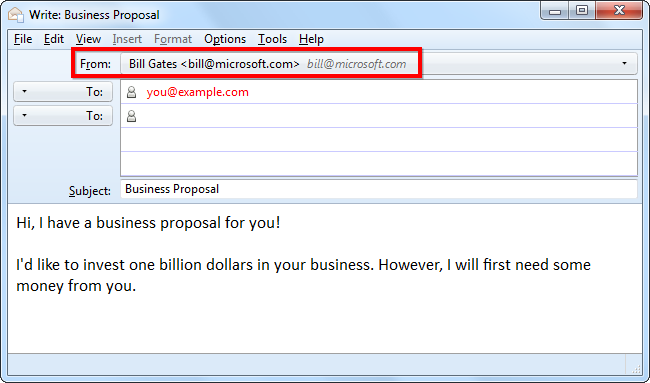
Emails with forged addresses may appear to be from your bank or another legitimate business. They’ll often ask you for sensitive information such as your credit card information or social security number, perhaps after clicking a link that leads to a phishing site designed to look like a legitimate website.
Think of an email’s “From” field as the digital equivalent of the return address printed on envelopes you receive in the mail. Generally, people put an accurate return address on mail. However, anyone can write anything they like in the return address field – the postal service doesn’t verify that a letter is actually from the return address printed on it.
When SMTP (simple mail transfer protocol) was designed in the 1980s for use by academia and government agencies, verification of senders was not a concern.
How to Investigate an Email’s Headers
You can see more details about an email by digging into the email’s headers. This information is located in different areas in different email clients – it may be known as the email’s “source” or “headers.”
(Of course, it’s generally a good idea to disregard suspicious emails entirely – if you’re at all unsure about an email, it’s probably a scam.)
In Gmail, you can examine this information by clicking the arrow at the top right corner of an email and selecting Show original. This displays the email’s raw contents.
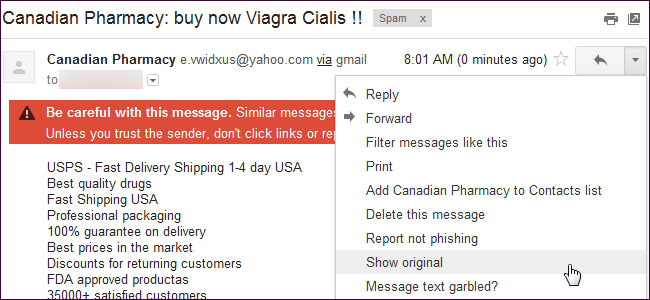
Below you’ll find the contents of an actual spam email with a forged email address. We’ll explain how to decode this information.
Delivered-To: [MY EMAIL ADDRESS]
Received: by 10.182.3.66 with SMTP id a2csp104490oba;
Sat, 11 Aug 2012 15:32:15 -0700 (PDT)
Received: by 10.14.212.72 with SMTP id x48mr8232338eeo.40.1344724334578;
Sat, 11 Aug 2012 15:32:14 -0700 (PDT)
Return-Path: <e.vwidxus@yahoo.com>
Received: from 72-255-12-30.client.stsn.net (72-255-12-30.client.stsn.net. [72.255.12.30])
by mx.google.com with ESMTP id c41si1698069eem.38.2012.08.11.15.32.13;
Sat, 11 Aug 2012 15:32:14 -0700 (PDT)
Received-SPF: neutral (google.com: 72.255.12.30 is neither permitted nor denied by best guess record for domain of e.vwidxus@yahoo.com) client-ip=72.255.12.30;
Authentication-Results: mx.google.com; spf=neutral (google.com: 72.255.12.30 is neither permitted nor denied by best guess record for domain of e.vwidxus@yahoo.com) smtp.mail=e.vwidxus@yahoo.com
Received: by vwidxus.net id hnt67m0ce87b for <[MY EMAIL ADDRESS]>; Sun, 12 Aug 2012 10:01:06 -0500 (envelope-from <e.vwidxus@yahoo.com>)
Received: from vwidxus.net by web.vwidxus.net with local (Mailing Server 4.69)
id 34597139-886586-27/./PV3Xa/WiSKhnO+7kCTI+xNiKJsH/rC/
for root@vwidxus.net; Sun, 12 Aug 2012 10:01:06 –0500…From: “Canadian Pharmacy” e.vwidxus@yahoo.com
There are more headers, but these are the important ones – they appear at the top of the email’s raw text. To understand these headers, start from the bottom – these headers trace the email’s route from its sender to you. Each server that receives the email adds more headers to the top — the oldest headers from the servers where the email started out are located at the bottom.
The “From” header at the bottom claims the email is from an @yahoo.com address – this is just a piece of information included with the email; it could be anything at all. However, above it we can see that the email was first received by “vwidxus.net” (below) before being received by Google’s email servers (above). This is a red flag – we’d expect the see the lowest “Received:” header on the list as one of Yahoo!’s email servers.
The IP addresses involved may also clue you in – if you receive a suspicious email from an American bank but the IP address it was received from resolves to Nigeria or Russia, that’s likely a forged email address.
In this case, the spammers have access to the address “e.vwidxus@yahoo.com”, where they want to receive replies to their spam, but they’re forging the “From:” field anyway. Why? Likely because they can’t send massive amounts of spam via Yahoo!’s servers – they’d get noticed and be shut down. Instead, they’re sending spam from their own servers and forging its address.

Good post for people that have to put their info over internet. Keep stuff that is really important off the web. Looking for more tips and strategies visit my site.
ReplyDelete